At its core, blockchains are decentralized ledgers that rely on cryptographic principles to ensure data is secure and unalterable. A key component that makes this possible are blockchain hashes.
This write-up explains how hashes and hash functions contribute to securing blockchain technology through ensuring data integrity, verifying transactions, validating blocks, and maintaining chain integrity.
It will also explore the latest developments of blockchain hashes, its biggest challenges, and what the future holds. So without wasting any time, let’s get started.
Key Takeaways
- Ensures Data Integrity: Hashes create unique digital fingerprints for data, making any alterations easily detectable, thus preserving the accuracy and authenticity of information.
- Verifies Transactions: Each transaction is hashed and linked to form a continuous and secure chain, ensuring all transactions are consistent and verifiable across the blockchain network.
- Validates and Secures Blocks: Hashes validate each block by linking it to the previous one, maintaining the blockchain’s integrity and preventing tampering.
- Maintains Immutability: Once data is hashed and added to the blockchain, it becomes immutable, making any unauthorized changes evident and protecting the data’s permanence and security.
Hash & Hash Functions in Blockchains
In blockchain technology, a hash and a hash function serve distinct but interrelated purposes. Together, these are essential for maintaining the security and integrity of a blockchain.
What is a Hash?
A hash is a fixed-length string of characters generated from an input of any size. They are generated using a hash function.
At their core, hashes ensure data integrity and verify the authenticity of information in a blockchain. Each hash is unique to its input data, meaning any alteration in the input will produce a different hash, thus making it easy to detect tampering.
What is a Hash Function?
A hash function is a mathematical algorithm that takes input data of any size and transforms it into a fixed-size string of characters, known as a hash. This transformation process is deterministic, meaning the same input will always produce the same output hash.
Hash functions are foundational to blockchain technology because they provide a means to securely encode data, enabling verification and validation within the blockchain network.
Furthermore, once a transaction in a blockchain is hashed, these hashes are used to create a Merkle tree – which efficiently summarizes and verifies the integrity of transactions.
The root of this Merkle tree is included in the block header, which is then hashed to create the block hash. This process ensures that each block is cryptographically linked to the previous one, forming a secure and immutable chain.
Note: Hashing is a one-way cryptographic operation, meaning once a transaction has been hashed, it cannot be reversed back.
We hope the following image clarifies this difference between the two.
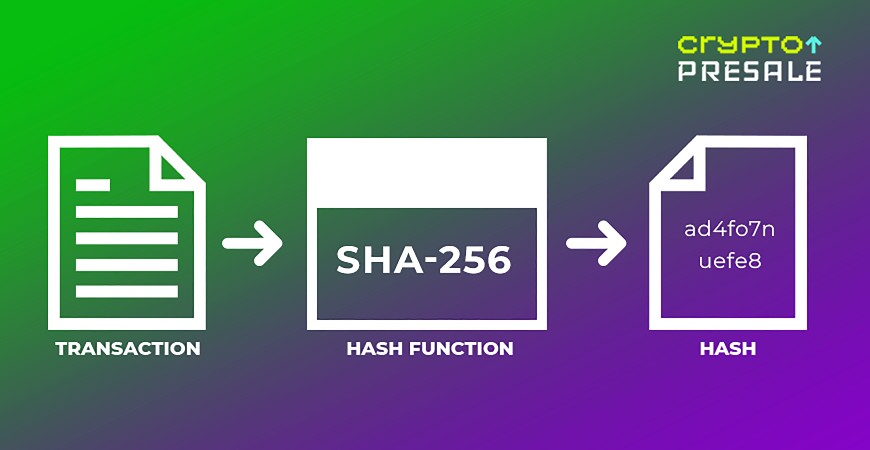
Characteristics of Hash Functions
- Function vs. Output: A hash function is the algorithm or process that generates a hash. The hash is the result or output of this process.
- Deterministic Nature: Hash functions ensure that the same input will always result in the same hash, which is vital for consistency in blockchain records.
- Fixed-Size Output: Regardless of the input size, hash functions produce a fixed-length hash, ensuring uniformity in data representation.
- Unique Output: Even the slightest change in the input data results in a vastly different hash, enabling easy detection of any data alterations (this is known as the Avalanche Effect).
- Collision Resistance: Well-working hash functions minimize the likelihood that two different inputs will produce the same hash, ensuring the uniqueness and reliability of each hash.
Hash Function Security
- Tamper Detection: Hash functions enable the detection of tampering. Any change in the input data results in a different hash, signaling that the data has been altered.
- Immutability: Once a block is added to the blockchain, the hash takes care of its immutability. This is because altering any data in the block would change its hash, which breaks the chain and signals that someone has tampered with it.
- Verification: Hashes allow for quick verification of data integrity. For instance, if you have a hash value and the input data, you can quickly check if the data matches the hash.
Interesting Fact: Modern hash functions like SHA-256 and Keccak-256 are designed to be resistant to known cryptographic security threats such as Birthday Attacks. This ensures that the blockchain remains secure, even as new vulnerabilities are discovered.
Types of Hash Functions and Their Uses in Blockchains
Below is a brief explanation of some prominent hash functions and their applications in different blockchains:
-
SHA-256 (Secure Hash Algorithm 256-bit)
SHA-256 produces a 256-bit hash value. It is part of the SHA-2 family, which is known for its robust security and wide adoption.
- Used in:
- Bitcoin
- Bitcoin Cash
- Solana
Keccak-256 (SHA-3)
Part of the SHA-3 family, Keccak-256 was designed to offer higher security margins and flexibility in output sizes. It uses a sponge construction, which makes it different from SHA-2.
- Used in Blockchains:
- Ethereum
- Ethereum Classic
- Binance Smart Chain
RIPEMD-160 (RACE Integrity Primitives Evaluation Message Digest)
This hash function produces a 160-bit hash value. It’s slower than SHA-256, however it’s still widely used due to its different cryptographic properties.
- Used in Blockchains:
- Dash
- Dogecoin
- Zcash
Scrypt
Scrypt is designed to be memory-intensive to resist ASIC mining, making it suitable for decentralized networks with lower power nodes.
- Used in Blockchains:
- Litecoin
- Digibyte
- Verge
Blake2b
Known for its speed and security, Blake2b produces variable-length outputs and is faster than MD5, SHA-1, and SHA-2.
- Used in Blockchains:
- Decred
- Handshake
CryptoNight
CryptoNight is designed to be CPU-friendly and ASIC-resistant, as it only relies on memory-bound computations. It is particularly used by blockchains that focus on privacy and ASIC resistance.
- Used in Blockchains:
- Monero
- ByteCoin
- Electronium
How Hashes Secure Blockchain Technology
Hashes are fundamental to maintaining the security and integrity of blockchain technology. Let’s take a detailed look at how hashes secure blockchain technology:
Data Integrity
Hashes create a unique digital fingerprint for each piece of data. Any modification to the original data results in a completely different hash, making it easy to detect alterations.
Beyond simple integrity checks, hashes are used in various cryptographic protocols, such as digital signatures and message authentication codes (MACs), which are crucial for secure communications and transactions over the blockchain.
Transaction Verification
Each transaction on a blockchain is hashed and linked to the previous transaction, forming a continuous string of blocks. This makes transactions verified and remain consistent throughout the network.
Moreover, this chaining mechanism underpins the concept of Merkle trees, which enable users to verify transactions without downloading the entire blockchain.
Block Validation
Each block in a blockchain contains a hash of the previous block, a list of transactions, and a nonce.
In public blockchains like Bitcoin, the process of finding a valid nonce that meets specific criteria is known as Proof of Work (PoW). This process validates the block and secures the blockchain by making it computationally impractical to alter any previous blocks.
Additionally, the difficulty adjustment mechanism in PoW ensures that blocks are added at a consistent rate, regardless of the total computational power of the network. This maintains the network’s stability and security.
Chain Integrity
Hash functions maintain the integrity of the entire blockchain.
Here, each block’s hash is based on its data and the hash of the previous block, creating an immutable chain. Due to this structure, any alteration in a single block would break the hashes of all subsequent blocks, making tampering easily detectable.
The interlinked nature of blocks also supports fork resolution mechanisms, where the longest valid chain is considered the true version of the blockchain, helping the network recover from splits and ensuring consensus among participants.
Immutability
Once data is recorded on a blockchain and hashed, it becomes immutable forever, meaning no one can alter it again. Any attempt to change the data will result in a different hash, breaking the chain and signaling tampering.
This characteristic is particularly valuable in applications requiring high integrity and transparency, such as supply chain tracking, voting systems, and legal document verification.
Immutable records provide an auditable and tamper-proof history that enhances accountability and trust in the blockchain ecosystem.
Tamper Resistance
Hashes provide a robust mechanism for detecting data tampering in the blockchains. This is because the hash of a block is derived from its data and the hash of the previous block, meaning any changes to the block’s data will alter its hash and break the chain.
Pivotally, this property makes it extremely difficult for malicious actors to alter data without being noticed.
Nowadays, advanced hashing algorithms such as SHA-256 are being deployed to detect collision resistance, meaning it’s practically impossible for two different inputs to produce the same hash.
Hashing – Real-World Applications and Innovations
It’s time now to have a brief overview of the current state of hashing in blockchain tech. Here’s what’s happening in the world right now.
Secure Hash Algorithms in IoT and AI
The integration of hash functions in IoT devices and AI systems is becoming more prevalent. This is because these sectors require hash functions that can operate efficiently on low-power devices, while ensuring high security.
More specifically, innovations in lightweight hash functions are addressing these needs, enabling secure data integrity and authentication within constrained environments.
Blockchain Scalability Solutions
Layer 2 solutions, such as the Lightning Network for Bitcoin, utilize hash functions to secure off-chain transactions. These solutions aim to enhance the scalability of blockchain networks by reducing the load on the main chain, while maintaining security through robust hashing mechanisms.
Hybrid Cryptographic Techniques
Combining different cryptographic techniques – including hash functions – to create hybrid solutions can enhance security and efficiency.
For instance, integrating hash functions with zero-knowledge proofs or homomorphic encryption can provide additional layers of security. Additionally, this also enables advanced functionalities like private transactions and secure multi-party computations.
IOTA, which is the world’s first distributed ledger for the “Internet of Everything,” is leading the pack in this regard.
The Biggest Challenge: Quantum-Resistant Hashing

Quantum computing poses a significant threat to traditional cryptographic algorithms, including hash functions.
This is because these computers, with their immense computational power, can potentially break current cryptographic standards by solving problems that are infeasible for classical computers. This has led to a surge in research that is focused on developing quantum-resistant hash functions.
NIST Post-Quantum Cryptography Standardization
The National Institute of Standards and Technology (NIST) is actively working on standardizing quantum-resistant cryptographic algorithms. In the hash function category, NIST is evaluating various candidates designed to withstand quantum attacks – where for example, algorithms like SHA-3 (and variants) are being scrutinized for their potential resistance to quantum decryption.
Lattice-Based Hash Functions
Lattice-based cryptographic methods are among the leading candidates for quantum-resistant algorithms. These methods rely on the hardness of lattice problems, which are believed to be secure against both classical and quantum attacks. Research in this area aims to develop lattice-based hash functions that can replace current standards if needed.
Multivariate Polynomial Hash Functions
Another approach involves using multivariate polynomials to create hash functions. These functions are based on the difficulty of solving systems of multivariate equations – which are problems that remain hard to solve, even for quantum computers. This makes them a promising candidate for quantum-resistant hashing.
What Does the Future Hold For Hashing in Blockchain Technology?

Let’s speculate on the potential developments that can drive this technology forward.
1. SHA-3 (Keccak) the Future Standard
In the future, SHA-3 will become the standard hashing algorithm for next-generation blockchains, especially those focused on high-throughput and scalability.
The integration of SHA-3 in zero-knowledge-proof systems should also be on the cards, which will improve privacy and reduce computational overheads.
Additionally, these will be used in conjunction with quantum-resistant algorithms, creating a hybrid cryptographic framework that addresses both current and future security challenges of quantum computing advancements.
2. Blake3 for High-Speed dApps
Because Blake3 can achieve even higher speeds on modern processors than Blake2, its efficiency and modern advancements in cryptographic hash functions make it an attractive choice for blockchain applications which require rapid data processing.
Beyond its immediate performance benefits, Blake3 will enable the development of more complex and scalable decentralized applications (dApps). This is due to its ability to handle larger volumes of transactions with minimal latency.
Blake3’s robustness in securing data will likely spur innovations in privacy-preserving technologies, potentially paving the way for more widespread adoption of confidential computing within blockchain ecosystems. This could then lead to the emergence of blockchain-based systems that support real-time analytics and instant micro-transactions.
3. The Implementations of Merkle-Damgård and Sponge Constructions
We believe the next generation of hash functions will implement Merkle-Damgård and Sponge Constructions.
Advanced implementations are expected to optimize these hash constructions to handle higher throughput and lower latency, indispensable for supporting the growing scale of blockchain applications.
Particularly, innovations in sponge construction will likely lead to dynamic hash functions that can adapt to different security levels and performance requirements in real-time, offering customizable security postures for various blockchain environments.
These developments will also integrate hardware accelerations and cryptographic coprocessors, significantly boosting the efficiency of hash functions on specialized mining hardware. This will also reduce the overall energy consumption of blockchain networks.
The Role of Hash in Blockchain Security – FAQs
What’s an example of hash security in action?
An example of hash security in action is Bitcoin mining, where miners find a nonce that produces a hash below a certain threshold to validate blocks and secure the blockchain.
What are the advantages of hashing?
- Data Integrity: Hashing makes sure that data has not been altered, providing a means to verify its authenticity.
- Efficiency: Hash functions are computationally efficient, allowing for quick processing of large amounts of data.
- Immutability: Hashing creates an immutable record of data, making it tamper-proof.
- Security: Hash functions are resistant to attacks, providing a high level of security for data.
Why is a secure hash function important?
A secure hash function is important because it ensures that data cannot be reverse-engineered or tampered with. This is of the utmost importance for maintaining the integrity and security of data within a blockchain.
Secure hash functions prevent collisions (where two different inputs produce the same hash) and ensure that any small change in input results in a vastly different hash, making it easy to detect tampering.
 Never miss an Update!
Never miss an Update!  Top Cryptos to buy?
Top Cryptos to buy?







